Hackers are using IP Hijacking to damage companies, organizations and governments in complete secrecy. To combat this, Shield-BGProtect has installed hundreds of sentinels worldwide, actively monitoring internet routing in general and routing to customer sites in particular. Utilizing Big Data analytics and proprietary algorithms Shield-BGProtect constantly analyzes the routes your data takes and examines potential threats to your internet traffic. It looks for potential interference with your communications and scrutinizes the ISPs you work with. Because of our active monitoring, we can detect all types of IP hijack attacks, regardless of the technique used. Ours is the only service in the world that can detect data-plane hijack attacks.
IP Hijacking is a serious cyber threat. Hackers reroute Internet traffic to their own lairs where they gain illegal access to traffic. Their dastardly plan is to copy, eavesdrop, and perform Man-In-The-Middle attacks plus other malicious manipulations, before returning traffic to the intended recipient. Other than a slight delay, your people won’t even notice their request took a detour. Successful access to Internet traffic also benefits hackers in their efforts to overcome measures put up to prevent penetration into target organizations. The consequences can be seriously damaging, especially since the victims are unaware it is happening.
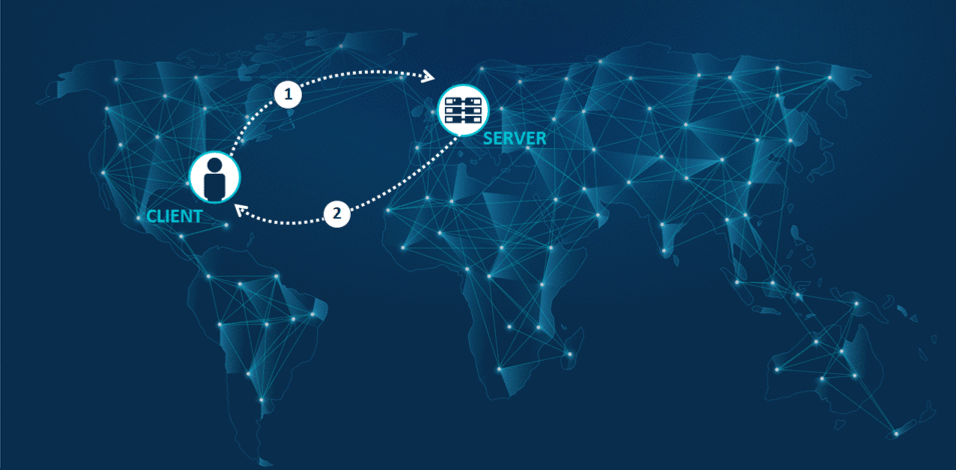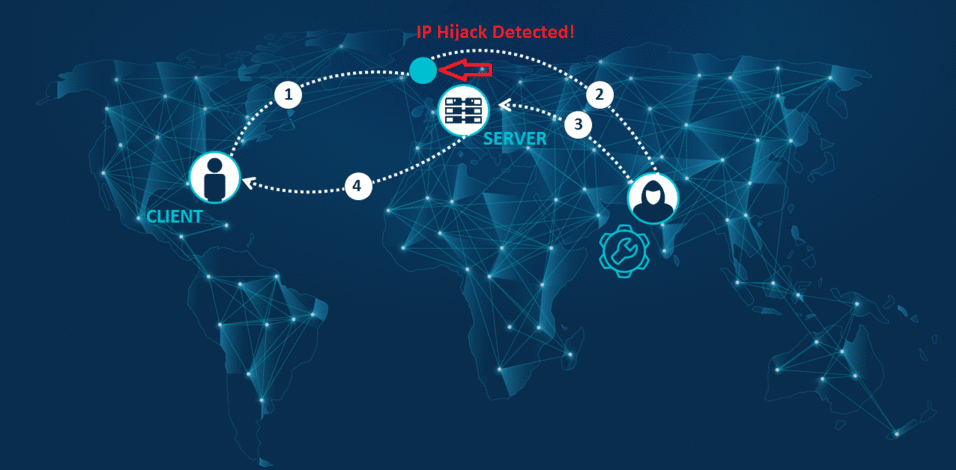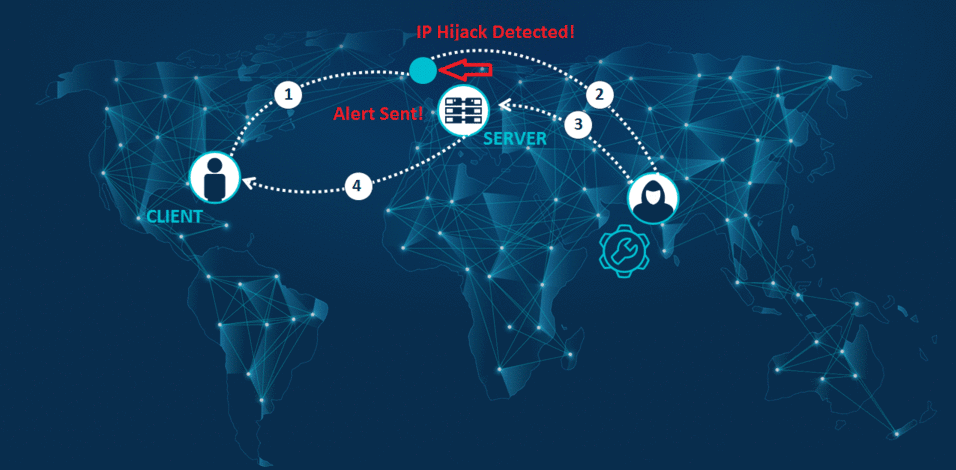
In addition, an attacker can hijack the IP address of a company’s service provider and spy on its intellectual property. This may include mail server traffic, VoIP and conference call traffic and Backup traffic.
IP Hijack attacks must be resolved at the ISP level. Once an IP Hijack attack is determined, Shield-BGProtect immediately informs the customer. We then work closely with the customer and the relevant ISPs taking full responsibility for managing the process until the threat is eliminated. Shield-BGProtect keeps the customer constantly updated with the progress and results of our intervention.
Attacks on internet traffic are difficult to detect, since damaging intervention occur in extremely short time frames. Only constant monitoring of all your traffic can identify and help mitigate these attacks. With Shield-BGProtect you get accurate detection of suspicious routing selections, discovering unexplained fluctuations in delay times and linking abnormal performance to possible hacking behavior. We can identify all types of hacking attacks on your internet traffic, regardless if they are short term, long term or intermittent.
Shield-BGProtect offers its solution as a SaaS product, so there is no complex integration, no racks of equipment and no additional manpower needed. Just give us your IP addresses and we’ll do the rest – including managing the mitigation process for you.